Entry statistics
0 צפיות
0 שבחים
Entry content
Entry content
Entry content
Entry content
Entry content

Entry content

Entry content

Entry content

Entry content

Entry content

Entry content

Entry content

Entry content

Entry description
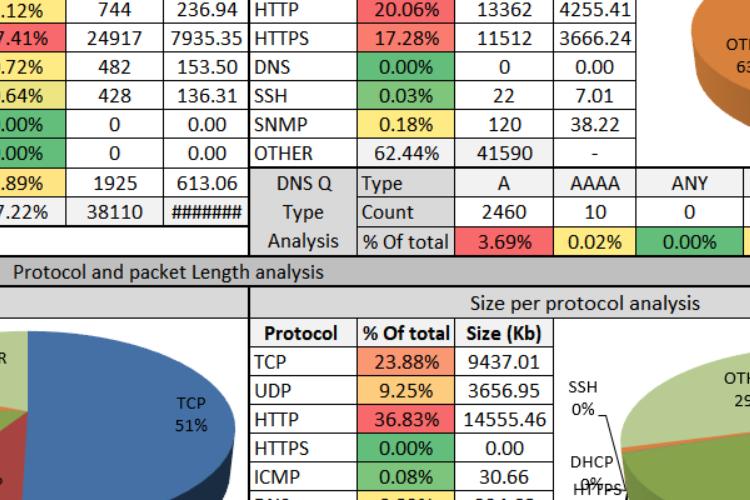
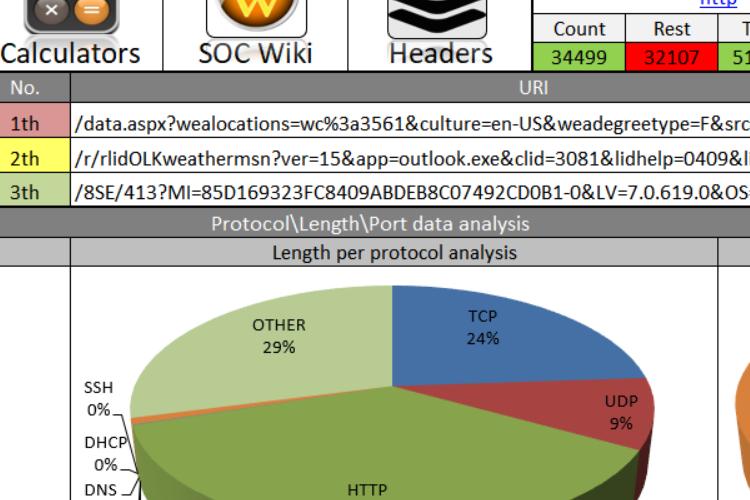
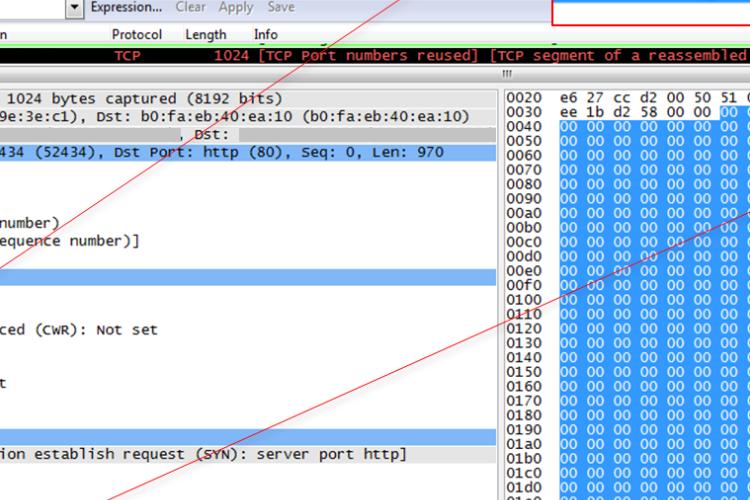
In this video we will thoroughly explain the "UDP-Flood" DDOS attack.
First, we will review some UDP fundamentals followed by IP Spoofing principle and finally, we will perform a real-life simulation of the attack, while noticing how it effects a station CPU and ICMP replies from the attacked machine.
First, we will review some UDP fundamentals followed by IP Spoofing principle and finally, we will perform a real-life simulation of the attack, while noticing how it effects a station CPU and ICMP replies from the attacked machine.
הוסף תגובה
0 תגובות
אנא
היכנס למערכת
כדי להגיב








 פרסום פרויקט
פרסום פרויקט


 התחבר עם פייסבוק
התחבר עם פייסבוק
 התחבר עם LinkedIn
התחבר עם LinkedIn
 0 צפיות
0 צפיות 0 שבחים
0 שבחים הוסף תגובה
0 תגובות
הוסף תגובה
0 תגובות